X.4 Certificates¶
1924 words on X.4 Overview
Back when X.3 was released, I was happy to see that Mail had gained the capability to sign and encrypt messages. The only difficulty in the process was that getting a certificate was a rather painful experience that required using a third party website and a Netscape web browser. As Safari improved, it became capable of downloading the certificates itself with version 1.2 in early 2004. That was great news at the time as it reduced the pain of signing your mail to battling with the certificate company’s website but reduced the things you had to do locally to downloading the certificate and double clicking it to let Keychain Access handle the rest of the work. Looking at X.4, it appears like the handling of certificates, encryption and your local keychain has seen a significant improvement, a few aspects of which I want to highlight here.
Keychain
A central but probably underestimated aspect of OS X’s encryption and password features is the Keychain Access application. Most users will only be familiar with the dialog boxes presented by the keychain infrastructure in the system which asks whether applications – mostly updated applications – are allowed to access the passwords in the keychain:
While they may be a bit annoying because you’ll be hassled a bit more frequently that you’d wish to be, I’ve always liked these requests as (supposing that Apple was willing and able to make them work as advertised) they give you a bit of control about where your passwords are going. In particular, when running your own computer at least, seeing such requests because an application was update when you didn’t do any updates may raise some suspicion.
For a while now, the dialogs for allowing access to the keychain could be expanded to reveal more information about who was requesting what. At many times the information given there wasn’t too enlightening or specific, though. In X.4 the UI for the expanded part of the dialogues has been cleaned up a bit and they’ll only show the name of the requested object and the requesting application rather than the path. But those names will be in the blue boxes which we started to see in X.3’s Mail for addresses and which are now standard Cocoa UI elements. Clicking those boxes will pop up a menu showing the application’s path, for example, and allow direct access to it.
While I still find what’s displayed in those dialogs a bit confusing at times, and I’m not entirely sure that their German localisations are understandable, it looks like we’re moving in a direction where things become clearer and more accessible.
Keychain Access
 While the standard keychain dialogue boxes are probably good enough for most days’ work as everything you’d want to do with your passwords can be done through these dialogues if the programmers of the applications you use put enough work in them, you’re really missing out if you don’t know the Keychain application which lives in the Utilities folder.
While the standard keychain dialogue boxes are probably good enough for most days’ work as everything you’d want to do with your passwords can be done through these dialogues if the programmers of the applications you use put enough work in them, you’re really missing out if you don’t know the Keychain application which lives in the Utilities folder.
To begin with, the previous paragraph isn’t quite true: You can’t delete passwords from the keychain using the standard interface. While the keychain is supposedly safely encrypted, you may want to do that as well and will have to use the Keychain Access application for that. In previous versions of OS X, the Keychain Access application used to be a bit of a pain. It would manage your passwords for servers, networks and other things as well as certificates for signing your own mails or verifying the signatures on other people’s. But was far from being effortless. Once a larger number of passwords and certificates had accumulated, managing or even finding them wasn’t fun.
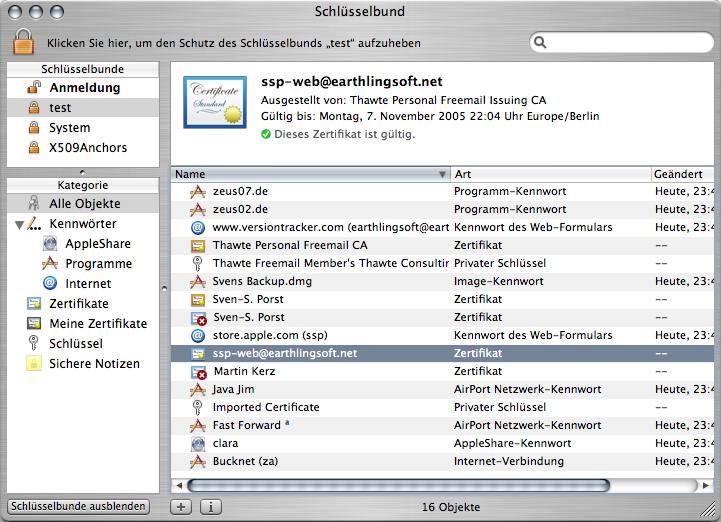
This has changed with X.4. Finally the Keychain Access application makes its power more visible. You’ll find the standard filter field which lets you quickly locate the item you’re interested in. You’ll find a number of categories at the left to just show items of a certain type (e.g. AppleShare password, Certificats, Keys or Notes which you can simply save securely into the keychain). And clicking an item will display a quick summary of it at the top of the window. All this looks quite familiar and reasonably easy to use:
When clicking the button at the bottom left of the window the pane seen at the top left will appear and list all keychains the system knows of. Your Login keychain will be the top one and the one your applications use. You can create additional keychains to put subsets of your keys or some note in – and make them accessible with a different password, say. The System keychain will contain keys that are used by the system, e.g. WEP keys for Airport networks. Finally the X509 keychain contains keys to verify the authenticity of others. As far as I can tell, when these tests fail Safari brings up the warning that the connection is encrypted but the other side cannot necessarily be trusted.
Double clicking any item in the list will open a new window – with some settings for the key you are using for keys, with information and setting regarding the certificate for certificates and with the option to view it for notes. Viewing the critical information will require you to enter your password – at least the first time.
Apart from the encrypted notes, those features have been present in previous versions of OS X as well. But they didn’t seem to be used much in the past. Perhaps they’ll find more users now that the Keychain Access application itself looks less scary.
My recommendation is to take a look at Keychain Access at least. You may be running into it at some stage. If you’re into acronyms, be sure to take a look at the application’s preferences and then report back what they mean. And there’s one more thing which looks like it could be both great and a bit strange. Right in the Keychain Access menu hides the menu item ‘Certificate Assistant’ which launches the application by that name that lives in ‘/System/Library/CoreServices/’.
Certificate Assistant
 The Certificate Assistant is a typical ‘assistant’ offering you pages of questions and trying to help you out with the answers. In this case the area of interest are certificates. And it’s a rather complicated topic, which is why the assistant offers buttons which reveal sheets with lots of extra information and explanation of the terminology on many pages. While I suspect that many people will feel overwhelmed by this, it’s probably the best you can do in this area. Crypotgraphy will not work if people use the tools ignorantly.
The Certificate Assistant is a typical ‘assistant’ offering you pages of questions and trying to help you out with the answers. In this case the area of interest are certificates. And it’s a rather complicated topic, which is why the assistant offers buttons which reveal sheets with lots of extra information and explanation of the terminology on many pages. While I suspect that many people will feel overwhelmed by this, it’s probably the best you can do in this area. Crypotgraphy will not work if people use the tools ignorantly.
The five courses of action offered by the assistant are to make your own ‘self signed’ certificate which sounds most interesting. You should be able to use it to make your own certificate which will automatically be added to your keychain to use for encrypting messages in Mail. This means that people can get into the Mail signing game more easily. On the other hand, you probably shouldn’t really trust the encryption by those certificates too much if the only contact you had with your e-mail partner was electronic. It’d be much preferable to meet in person to exchange certificate or verify the certificates’ fingerprints (which can be seen in Keychain Access of course). Perhaps ‘phoning’ people via iChat could be an option to get that ‘in person’ verification but with just a tiny bit of paranoia you’ll consider that unsafe as well. Unfortunately this hasn’t really worked for me yet, potentially because of the other certificates that are in my keychain – it’s not really transparent what’s happening there.
Next is to make your own certification authority, meaning that you’ll, thirdly, be able to generate certificates for others – potentially useful if you’re making certificates for a circle of friends or your company. What’s particularly nice about that is that generating your own certificate authority will generate a configuration file which you can send to people and they only have to double click (in case they’re running X.4., I guess) to invoke the Certificate Assistant with the correct options. Not that I really know what I’m doing, but feel free to give my file a shot and we’ll see what happens. Note that the Certificate Assistant seems to include an SMTP agent that e-mails your request away. More critically, it doesn’t tell you that there is a problem when there is no internet connection available to send the message over. I suppose requests made when being offline are just lost.
Then there’s an item to request a certificate from an existing authority. I haven’t tried it, but it seems to ask you for all the information needed for a certificate and then e-mails an appropriate request to a certification authority, the address of which you‘ll have to provide, though. The last option lets you view and verify existing certificates.
This assistant looks like a rather powerful tool with many hard-to-understand options. I’m not an expert in cryptography and how to implement it properly. But Apple certain made an effort here. I hope they did a good job as well.
Safari
Safari’s skills in dealing with certificates – used for the encrypted connections to web sites – have been improved as well. The well known dialog which Safari uses to complain about untrusted certificates can now be extended to display the certificate. And you can ask Safari to always trust this particular certificate.
Passwords
 When looking around Keychain Access or other places of the system where passwords need to be generated, like the Users preference pane, you’ll notice another new feature of X.4. There’s a little key button now which will open a palette that helps you make a good password. To begin with it has a little control that tells you how good the password you entered is. If it isn’t good enough it’ll offer some hints of the ‘use non-dictionary words’ or ‘use numbers and punctuation’ kind.
When looking around Keychain Access or other places of the system where passwords need to be generated, like the Users preference pane, you’ll notice another new feature of X.4. There’s a little key button now which will open a palette that helps you make a good password. To begin with it has a little control that tells you how good the password you entered is. If it isn’t good enough it’ll offer some hints of the ‘use non-dictionary words’ or ‘use numbers and punctuation’ kind.
It goes even further in that it has a menu listing different ways to generate passwords – from random ones to easily memorisable ones based on dictionary words. You can pre-set the length you want and the tool will tell you how secure the generated passwords are. I swear that the combination of the railway service and cholera in the screen shot have been randomised up by the software.
Address Book
The final thing I want to mention is a little improvement to the Address Book application.
 In X.4 it will put a little check mark next to e-mail addresses that you have a certificate for. That’s nice and may save you a trip or two to Keychain Access. Particularly with Mail not giving any information on which keys it uses and where they come from, this can be useful information.
In X.4 it will put a little check mark next to e-mail addresses that you have a certificate for. That’s nice and may save you a trip or two to Keychain Access. Particularly with Mail not giving any information on which keys it uses and where they come from, this can be useful information.
Double clicking one of the checkmark will display a sheet with information about the certificate. This would be nice if it weren’t buggy and displayed only the first certificate that it finds for the address in question: Most certificates are valid for one year only. Thus you’ll end up having a couple of them for each e-mail address. And Address Book should display all of them or at least the current one rather than displaying an old one saying that it has expired.
Another strange thing is that the Address Book will display a check mark for certificates which exist but which Mail will not use. It’s not entirely clear to me what’s going on there and why.